VPN vs. Tor: Everything You Need to Know
VPN vs. Tor: Which one should you choose and why?

A CBS news article published in early July 2020 warned that VPNs have come under threat. Covid-19-related office closures have forced more people to work from home, and as malicious entities take advantage of lax home networks they are finding ways around VPNs.
According to the article, an NSA official warned that “VPNs are particularly prone to attacks”, and network administrators should pay attention to “ports, protocols, and IP addresses of network traffic to VPN devices.”
A few days after this article appeared, the University of California in San Francisco was forced to pay more than $1 million to cyber attackers. They had taken over their network and demanded money before they could release it back to them.
This attack proves what the NSA is warning us about – that even those of us with top-notch security, like institutions of higher learning, are susceptible to data breaches.
Increasing online security threats have forced many of us to rethink our security. For some, an antivirus and a firewall are enough. For those who are serious about remaining anonymous and secure online, Tor and VPNs are good options.
Threats to VPNs aren't new. New ones arise all the time. Fortunately, the best VPN companies are vigilant, and they are able to quash any threats before they become a problem.
That said, users want to have options. Although they have access to VPNs, they want to know how else they can stay anonymous and secure online. Hence the question of VPN vs. Tor.
VPN and Tor are not direct competitors. They are both online security solutions. The one you choose depends on what you do online and what kind of security works best.
The best way to answer the VPN vs. Tor question is to understand what they are and how they work to provide security.
Table of Contents
What is a VPN?
VPN stands for Virtual Private Network. It allows you to connect to servers through restricted channels so that no one can see what you are doing or where you are. In countries like Russia, China and Cuba, many people use VPNs because they allow access to restricted websites – what is called geoblocking.
VPNs were created they were meant to connect businesses securely over the internet. Today, anyone can use a VPN and enjoy the benefit of security and anonymity.
When you turn on your computer and go online you are out in the open. Anyone with the right software and a little bit of skill can see what sites you are visiting, the data you are sending to and requesting from these sites, what times you log on and off, where you are and so on.
This is the stuff that hackers live for. All the personal information they collect from breaking into personal computers can be used for all manner of things.
With your credit card information, for example, they can make unauthorized purchases and bleed your bank accounts dry. Any other personal information they find can be used for blackmail and extortion.
It's not just criminals who are interested in this kind of information.
Many businesses are built around collecting user data. They troll computers and gather personal information that they sell to advertisers.
Sometimes when you buy an item online you'll see similar items on your social media feeds – ever wondered how they knew what you bought? They can track your online activity, see which sites you visit and what you buy.
ISPs also track online activity, and they can see what you do and when you do it. Streaming companies like Netflix are able to track down unauthorized streaming.
Governments can track you down using your online activity. In countries where freedom of the internet is restricted, those who visit certain online locations can be tracked down by simply looking at their online activity.
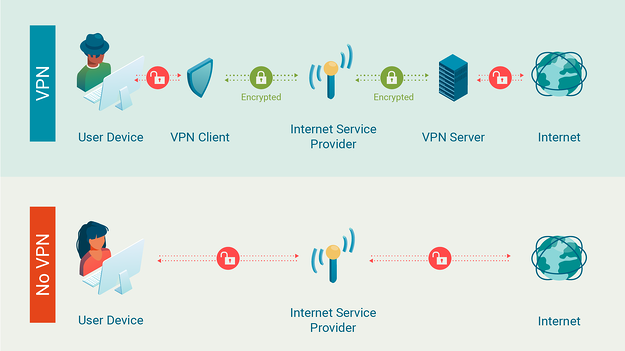
If you have a VPN installed on your device you can bypass all these issues.
How Do VPNs Work?
One of the questions that most people ask before they start using a VPN is – how does a VPN work?
Every time you type a query into your computer it's sent to a server. The query is sent through several servers before you can get a result on your device. Throughout the relay process, the query is out in the open, and with a little bit of expertise and some basic software, anyone can see it.
The same goes for answers to your query. When the answer to your query is found, it's sent back the same way – through a series of servers – and anyone can see it.
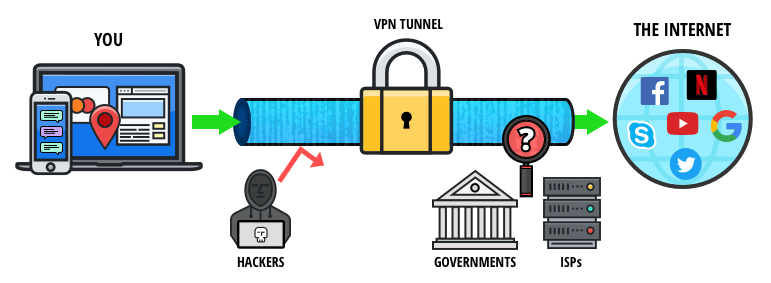
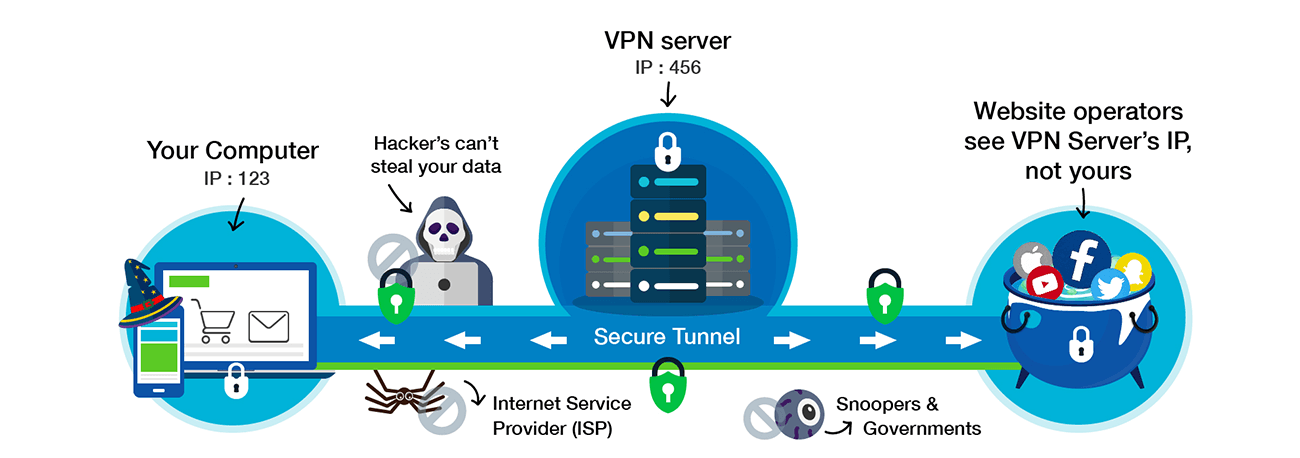
A VPN secures your connection both ways by providing a safe tunnel for it to travel through. Your query is encrypted before it leaves your device and the answer is encrypted before it comes back. When it arrives at your tablet, phone or computer it's decrypted.
When you install and turn on a VPN, it creates a secure tunnel between your device and remote servers. This tunnel is secure from prying eyes – no one can see what you are doing online, when you do it or where you are doing it from.
The best VPNs encrypt data using the latest technologies. In case the security of the tunnel becomes compromised and data falls into the wrong hands all a hacker (or anyone else will see) is gibberish.
VPNs also assign your device a different IP address from your real one. When you send a query through a VPN, it goes to a server that's part of the VPN network. These servers hold tens of thousands of IP addresses. They are randomly assigned to users every time they log on.
If anyone tries to find out who you are by looking at your IP address, all they'll see is an IP address assigned by the server you connected through. They can try and track you down, but they will not be successful.
Most internet protocols already have built-in protections (HTTP, SSH etc). These encrypt your data at least once. When you add a VPN, you have two levels of protection.
What VPNs Will Not Do
When discussing VPN vs. Tor, it's important to look at what each can do and where they encounter limitations.
There are certain things that even the best VPN won't do. There are lots of ways to track online behavior. Cookies, for example, are used all the time to track online behavior even after you leave a website. Apart from this, there are certain VPN limitations that you should be aware of:
VPNs keep user logs
Most, if not all, VPNs keep user logs of one type or another. Logs are company records of user activity that can be used to track your activity. These logs serve to improve user experience, and they are deemed necessary for smooth running of a VPN service.
While most VPNs collect user data of some sort, the best ones minimize risk by taking certain steps:
- They make sure that they are not in a jurisdiction that has signed any data-sharing agreement.
- These companies collect only minimal information. They may only keep the email address you used to sign up and your credit card number, as well as downtimes experienced by users.
- They destroy user information after brief cycles – every month or every few weeks – so that if the government comes knocking, they don't have much to hand over.
Some sites automatically block VPNs
Some organizations view VPNs as suspicious entities and lock them out altogether. Their systems have software that can detect data from VPN servers, and they block it out.

This can be costly. Imagine if your bank, or your doctor, tries to send you an email that fails to reach you because of a VPN.
Anti-VPN technology is improving
It's in the interest of certain companies to develop software that can go around VPN technology. Netflix is a good example.
If you connect to Netflix using a VPN, you may wake up one morning to find that it doesn't work anymore. It's because Netflix has found a new way to block access through VPNs – they want you to pay for content.
VPNs are in a race with anti-VPN technology, and sometimes they lose.
VPNs are in it for the money
Companies that make VPN software are not charities. They are companies that are out to make money, and they will often do whatever it takes to turn a profit.
Some secretly sell user information to advertisers, others do not invest in the best encryption and there are some that limit server numbers and slow down speeds.
As a user, there is no way to check the claims that these companies make. You have to take them at their word and hope for the best.
Some VPNs will slow down your internet connection
A VPN can slow down or speed up your internet connection, but in most cases you'll experience slightly slower speeds.
Speed can be affected by your VPN server. The farther away a server is, the slower your connection is likely to be. If a server has a lot of traffic, each client connected through it will experience slower speeds.
The best VPNs automatically choose ideal servers for clients. When you log on, they connect you through the nearest and least congested server to ensure that your internet speed remains unaffected.
The level of security you choose will also affect your speed. The higher the security, the slower your connection is likely to be. If you use AES-256 encryption (the best) you'll notice a lag in connection speed.
To get around this you can choose a lower level of encryption. You should also work with an ISP that offers high speeds. That way, when there is a small lag in internet speed you'll barely notice it.
Beware of free VPN services. While they may offer you protection, many have a limited number of servers for non-paying users. The strain created by many free users logging on at once slows down connection speeds.
What is Tor?
Tor stands for The Onion Router. It's an online privacy tool developed by a non-profit organization of the same name that researches and improves online privacy. It's available for use on Windows and Mac, Linux and most mobile devices. You can download the Tor browser directly on your computer and mobile device.
For android devices, Tor is available in the Google Playstore under different names including OrBot and OrFox. Apple users can download Tor from the Apple app store by searching for OnionBrowser.
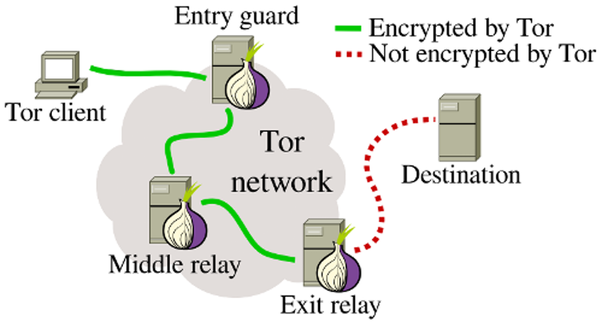
Tor's main objective is to protect your identity whenever you're online. When you log in through the Tor network, all your activity is encrypted and no one can see it.
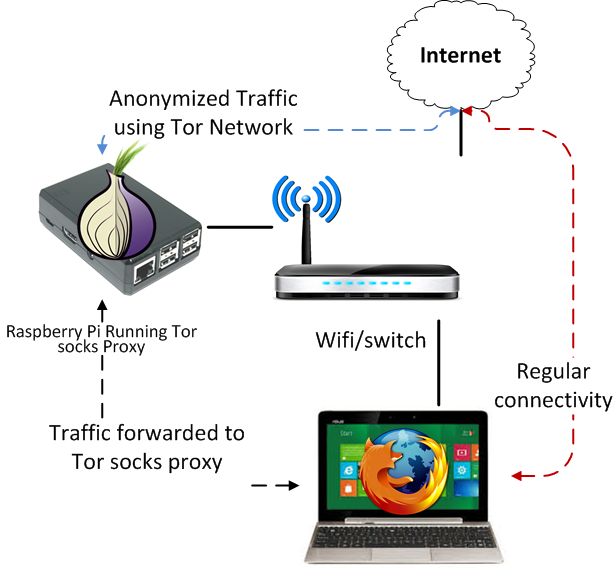
The US Navy, in conjunction with independent researchers, created the Tor network in the ‘90s. Although it still receives some support from its creators, it has evolved into open-source software that's run by a non-profit organization.
How Tor Works
Tor works by anonymizing your online activity in steps. It comprises three layers. As data goes through each it is encrypted and anonymized. Remember Tor stands for The Onion Router? The three layers are like the layers in an onion.
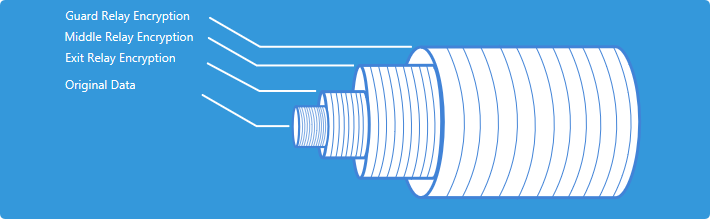
You need two elements to get Tor to work: the software and the network of servers that hosts the network.
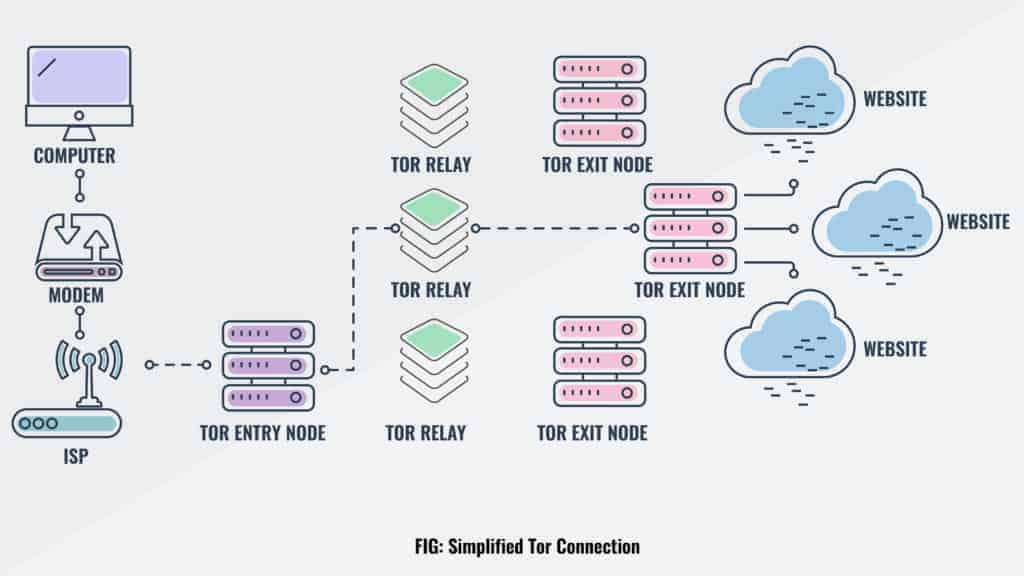
The easiest way to understand Tor is to think of it as a series of computers. When you send a request through this network it's bounced through a series of other computers (which are called relays) and encrypted.
These relays are a series of volunteer servers that are operated by individuals and organizations across the globe. The more servers present within the Tor network, the faster and more robust the network is. More computers mean more bandwidth among users.
Another advantage of having more relays is that it becomes harder to track users – they are bouncing data between many different points, making it almost impossible to keep track on.
Any computer can become a Tor relay, and no special software or hardware is needed. All you need to do is download Tor and configure your computer to act as a relay.
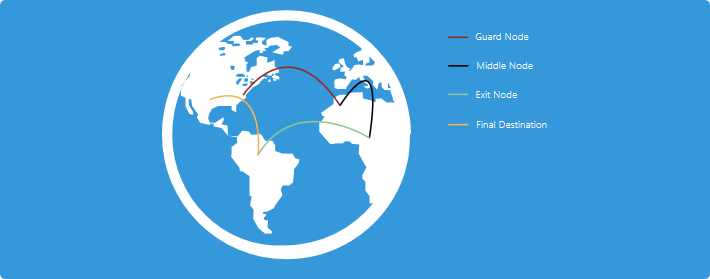
Each Tor connection bounces through 3 different types of relays, and each has a specific job to do.
The first, the guard or entry relay, is the entryway into the Tor network. Not all servers can become entry relays. They are usually selected depending on how long they have been around and how stable and reliable they are. They must also have a high bandwidth.
The middle relay is where data goes after it leaves the entry relay. These relays serve two purposes. The first is to add encryption to all information that passes through them. The second and more important function is to make sure that the first and third relay never “meet”. If these two relays were to communicate, it would make data easier to track.
The third and final relay is the exit relay. These send data back to the client who requested information.
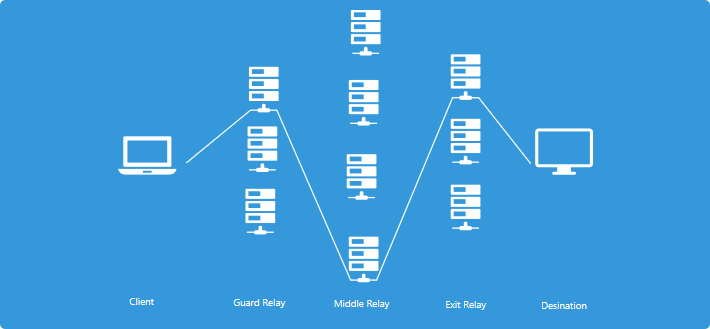
Data is most vulnerable at the exit relay. Most illegal Tor activity is tracked at this point because this is where information is sent to the end destination.
Is Tor Legal?
The use of Tor is legal in most countries. However, countries that discourage free use of the internet and free speech do not generally encourage the use of this network as it allows access to sites that are banned. These countries invest in traffic that blocks all Tor software.
The use of Tor is banned In China, Russia, Saudi Arabia and Iran, and the governments track and stop Tor traffic, but some people are still able to get around whatever hurdles are in place.
In most other countries it's perfectly legal to use it. However, if you are doing something illegal on the Tor network you can be arrested and prosecuted to the full extent of the law.
Silk Road is/was considered to be one such activity. Members of this group trade illegal items like guns and drugs, and when caught, they are prosecuted and jailed.
How Secure is Tor?
Tor is very secure. Because data bounces between so many nodes it becomes almost impossible to track.
The other thing that makes Tor secure is the fact that the different relays don't communicate with each other. At each relay, it's allocated a different, random IP address, so trying to find out where it came from or where it's going is extremely difficult.
That's not to say that the system is foolproof. One of the biggest concerns about the Tor network is that servers are run by volunteers. You have no idea who's running the relays you're using.
The weaknesses at exit nodes are also cause for concern.
Weaknesses of Tor
The biggest problem with Tor is that it slows down internet connections. As traffic bounces from computer to computer internet connections slow down. If you plan to start using Tor, prepare for internet searches to become slower.
There are other weaknesses of this network:
- The traffic between your computer and exit relays is trackable. If someone is determined, all they need to do is a statistical analysis to find out your IP address.
- Exit relays have IP addresses that are known. Some ISPs block traffic from these IP addresses. This is how governments and intelligence services block Tor traffic.
- ISPs can see when you are using TOR and they can block you.
VPN vs. Tor – Which is More Secure?
Both VPNs and Tor provide online anonymity, and they each have pros and cons. While Tor is free and provides multiple levels of data encryption, it is slow.
Tor is also associated with a lot of illegal activity, and if you aren't using it for strictly legal purposes you may end up in lots of trouble.
We recommend that you always use a VPN. They encrypt traffic and have additional measures to prevent hackers from accessing your devices. They are also fast and you can use them to access any site.
The most secure system uses a VPN at all times. Ordinary traffic, like bank transactions and everyday searches, can be protected through a VPN connection. When you want an additional layer of anonymity you can log in through the Tor network.
You can use Tor and a VPN at the same time, but it will slow down your connection significantly. This kind of setup is useful for those who worry about Tor traffic from the exit node to the destination device.
A VPN will hide the fact that you are using Tor, and no one will see what data goes in and out of the network. For some, this added layer of protection is worth the slower speeds.
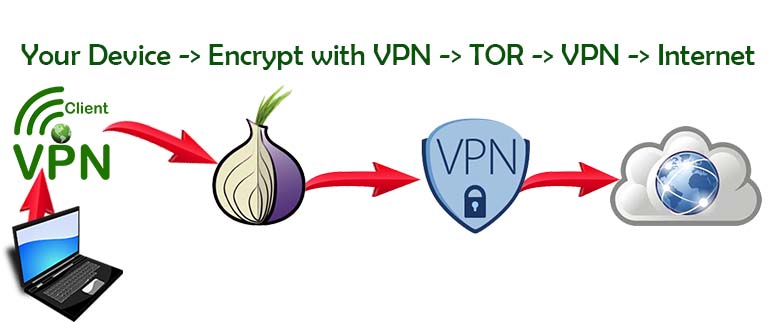
When to use a VPN vs. When to Use Tor
There are no clearcut guidelines in place for when to use a VPN and when to use Tor. It all depends on you and what you hope to achieve. Most people choose VPN over Tor because it doesn't significantly affect internet speed.
There are some special circumstances when a VPN is recommended:
- When you want to bypass geoblocks without interference from your ISP.
- VPNs are effective for preventing data leaks and cyber attacks
- Those with a slow internet connection will do better with a VPN than Tor.
- If your ISP is throttling bandwidth, you can bypass the problem by connecting directly with servers instead of going through your ISP.
- VPNs are recommended for anyone who uses public Wi-Fi or unsecured networks.
- Before you transact any money online, install a VPN to keep your details safe from hackers.
Recommended VPNs
|
VPN |
Number of Servers |
Number of Devices |
Kill Switch |
Stream Netflix |
User Logs |
Jurisdiction |
Price (Monthly) |
| 1,600 | 10 | Yes | Yes | No | United States | $4.99 | |
| 3,200 | Unlimited | Yes | Yes | No | British Virgin Isl. | $12.95 | |
| 7,100 | 7 | Yes | Yes | No | Romania | $12.99 | |
| 5,400+ | 6 | Yes | Yes | No | Panama | $11.95 | |
| 3,000 | 5 | Yes | Yes | No | British Virgin Isl. | $12.95 | |
| 700 | 5 | Yes | Yes | No | Switzerland | $12.95 |
For more in-depth comparison of the best VPNs click here.


