VPN vs. Proxy: What’s The Difference & Which One Should You Use?
Most people know what a VPN is. They even have a fair idea of what the TOR network is. But if you ask about VPN vs. proxy, they have no idea what a proxy is and so they cannot make comparisons.
In this VPN vs. Proxy post we'll look at what is a VPN, what is a proxy, how they compare and which one you should use.

But before we do, let's quickly talk about why we need internet security. Why do we bother with VPNs, proxies or even Tor?
Table of Contents
Why Do You Need Online Security?
When we need something from the internet we look for a device, open a browser and type in a search query. We rarely stop to think about whether our searches could deliver compromising information into the wrong hands.
When most people think about data breaches they think of data hacks into company databases. It doesn't occur to them that hackers can target individuals.
Consider these statistics about online security breaches:
- According to a study at the University of Maryland, a hack occurs every 39 seconds. Your computer or mobile device might be under attack multiple times a day.
- In more than 60% of the cases, it takes at least a month to discover a data breach.
- A full ID package costs between $30 and $100 on the internet black market.
- A 2018 report indicates that more than 50% of all data breaches originate on social media.
What does all this mean? It means that we are all at risk. If a computer gets hacked every 39 seconds, and an ID pack can sell for $100, it may be only a matter of time before you fall victim to online hackers and other malicious entities.

Hackers aren't the only reason why people use VPNs, Proxies and Tor.
A lot of times they implement these tools because they want to be able to go online anonymously. Many live in countries that implement geoblocking against their citizens, while others want to be able to access otherwise unavailable websites. Netflix and other streaming sites that limit content based on location have forced many people to buy virtual private network software.
Some people use these security tools because they would like to keep their online activity private for personal reasons.
Do You Need a VPN?
If you haven't taken active online security precautions, it's time you did. It may only a matter of time before you have to deal with the debilitating effects of a data breach, and depending on how extensive it is, it can take years to recover.
Now that we have that out of the way, let's look at VPN vs. proxy in detail.
What is a VPN?
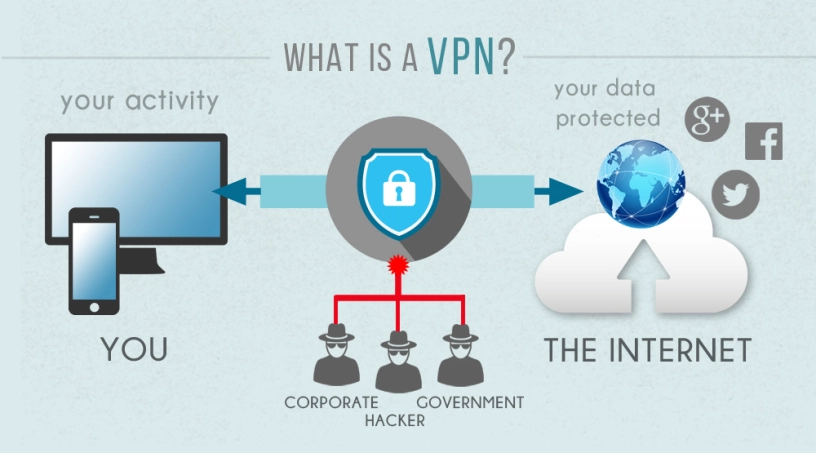
VPN stands for Virtual Private Network. It is software that encrypts data and hides your IP address to ensure that you are anonymous and protected at all times.
Each time you are online your activity is detectable. Anyone with a basic understanding of internet security and a hacking tool can see what you are doing, where you are doing it from and even the kind of device you're using.
With a VPN you are anonymous. The best VPNs use several security measures to ensure that all data that passes through their software is secure.
VPNs Encrypt Data
Each time you go online, the data that you send out to search engines is visible by various entities. Think your ISP, government agencies, hackers and so on. A VPN encrypts data, and anyone tracking your online activity cannot see what you're doing.
It does this by encrypting all information. Even if your traffic is visible, it's nothing more than a jumble that's almost impossible to decrypt.
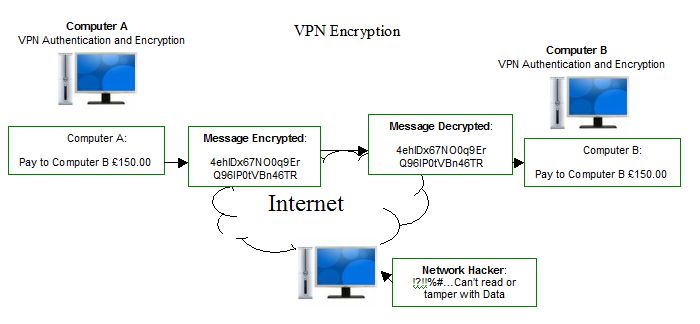
Incoming data into your device is treated the same way – it passes through a secure tunnel and is only decrypted after it arrives, so no one else can see what it is.
If someone were to steal your data, they will not be able to do much with it because VPNs use complicated encryption algorithms, usually the same that are used by intelligence agencies.
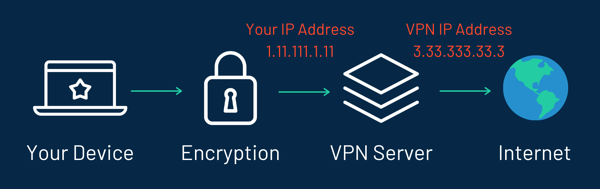
VPNs Mask Your IP & Help Bypass Geoblocks
One of the most important things that a VPN does is to hide your IP address. Each time you are online your ISP and anyone else who is keeping tabs on you can see your IP address.
Your IP address works a bit like a postal address – it can tell people the exact location of your device. If they can find your device, they can find you.
Have you ever wondered how your ISP throttles bandwidth when you're doing activities like streaming or torrenting? They can see your IP address and your internet activity, and based on that they decide to allocate you lower bandwidth. A VPN will help you avoid this.
VPNs at Bypassing Geoblocks.
Each time you use a VPN to go online your information goes through a server that belongs to the VPN company. Each of these servers has thousands of random IP addresses that they assign to every client. Anyone who tries to trace you using your IP address is led back to the VPN server.
VPNs Prevent Malware, Trackers & Malicious Code
Many people install a VPN so as to avoid getting infected with malicious code. Many websites have code that can infect devices and collect personal information. A good VPN will block these sites and ensure that your devices are protected.
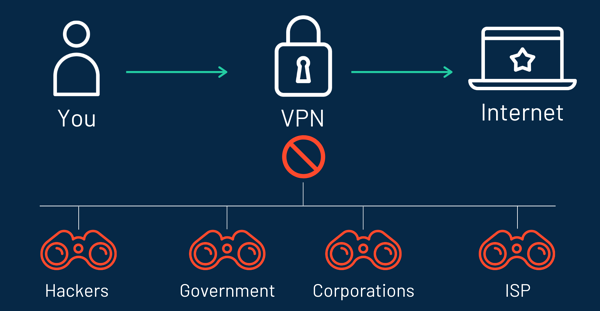
It will also stop trackers that could be crawling your devices to gather information.
Sometimes when you visit certain sites, you're later served with ads related to the products or services you were looking at. How do these ads know what you've been looking up online? They install trackers and sell the information they collect to advertisers.
A VPN blocks such trackers, and websites cannot collect certain types of information from your devices.
Do VPNs Make You 100% Safe?
Unfortunately, VPNs are not 100% secure, but they are usually enough to deter hackers, government overreach and anyone who may be trying to track you online. Some companies (like streaming companies) actively develop anti-VPN software that can bypass security measures.
When shopping for a VPN there are several important factors to keep in mind to ensure that you get ultimate protection:
- No IP address leaks – VPNs are supposed to hide your IP address, but some are flawed and they can leak your address. There are ways to check whether a VPN leaks IPs. It helps to check user reviews to see whether there have been complaints of this nature against the VPN you have in mind.
- No logs – this is a big issue with VPNs. It's counterproductive for a VPN to keep a record of your online activity. If this information falls into the wrong hands it can cause unnecessary headaches. Sometimes governments subpoena records from VPN companies, and if there are logs they can be used for prosecutions. All leading VPN companies claim that they do not keep logs, but verify before you buy. Look at the kind of information they keep. It should be minimal and should not facilitate client tracking.
- Privacy policy – privacy policies are long and boring but when it comes to VPNs they are worth looking into. In many cases, the fine print of the privacy policy is quite different from the marketing material, and if you suffer a security breach you'll only have yourself to blame.
- Kill switch – if your VPN connection drops your details can leak. The best virtual private network software has an in-built kill switch, and each time the connection drops you're immediately taken off-line to prevent leaks.
VPN vs. Proxy: What is a Proxy?
Proxy servers aren't very common; they are viewed by many as an old-fashioned online security strategy. However, many companies still direct their traffic through proxies in an effort to control what goes in and out of their networks.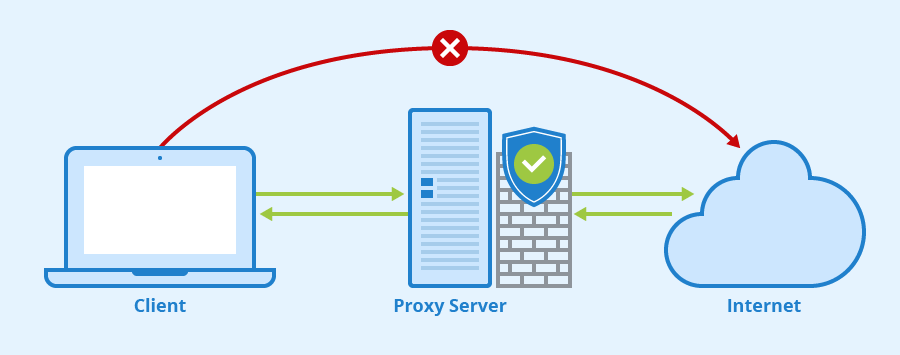
What is a Proxy Server and How Does It Work?
The easiest way to think of a proxy server is as a gateway that stands between you and the internet. All the traffic within the network flows through the server before it's sent to external servers to fetch requested information and vice versa.
After the request is fulfilled it comes back via the same route…through the proxy server where it's vetted before it's forwarded to the end-user.
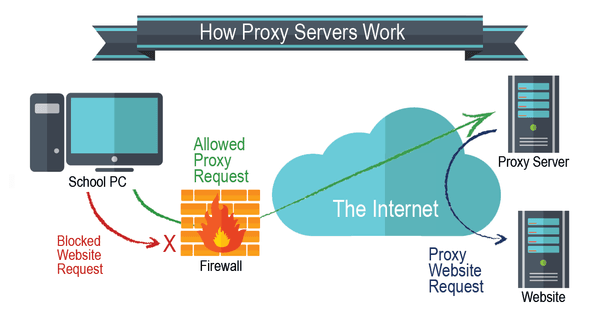
That doesn't seem like very much by way of security especially when compared to systems like VPNs and Tor. So why do some insist on using proxies?
The answer is simple: proxy servers provide a high level of security for business networks.
A modern proxy does more than act as a conduit for web requests. It connects everyone within the network, acts as a firewall and blocks all “bad” web content from networks.
Every computer that is connected to the internet has an IP address, and each IP address is unique – it works like a home address. The internet uses the IP address to deliver your searches back to you.
When you send out a request, the IP address of the device you used is attached to the request, which is how you get the information you requested delivered back to your computer.
A proxy server acts as a middleman between your device and the internet. It knows the IP address of every device that's connected to it.
When you send out a request, it goes through the proxy and is assigned the IP address of the proxy. Anyone looking at the request will not see your IP address – they will see the IP address of the proxy instead.
The response to your address is passed through the same channel – first to the proxy and then on to your computer.
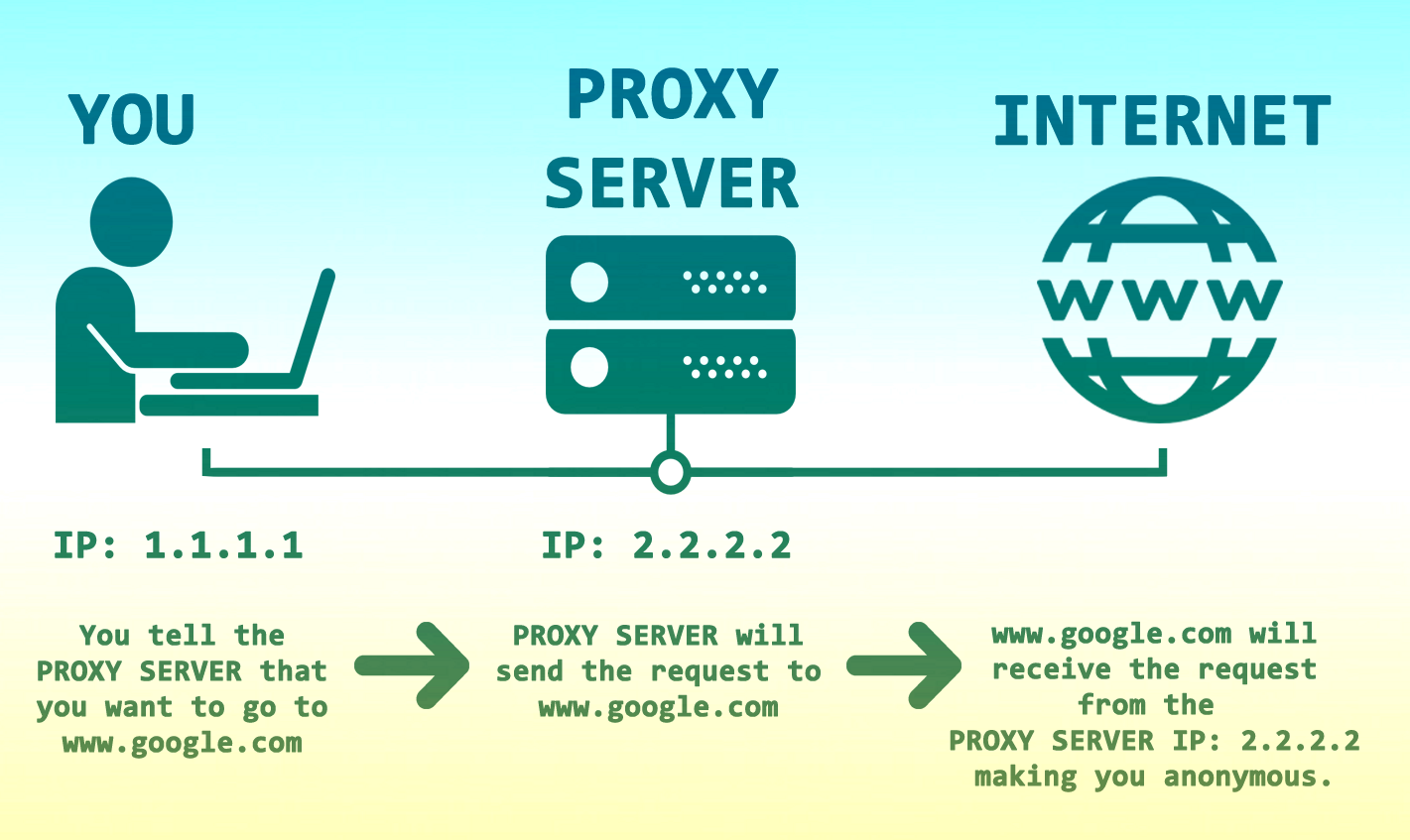
A proxy can make changes to data sent through it. It can, for example, encrypt it and make it unreadable as it travels through web servers.
What Are The Benefits of a Proxy Server?
- The biggest benefit of using a proxy server is that it hides IP addresses. An IP address can reveal a lot about your online activity. VPNs do this as well because they realize how unsafe it is to have visible IP addresses.
- A proxy server can help you bypass geoblocks. A geoblock is when you are prevented from accessing certain sites because of your location, which is based on your IP address. Because information requests are assigned the IP address of the proxy server they look like they are coming from a different location.
- Proxies often help make systems faster. Certain pages are visited quite often by proxy server users. The information from these sites is cached and this helps reduce load times.
- A proxy can be used to block malicious sites. The admin can list any site that they consider unsafe on the server so that if anyone within the system tries to access it they are unsuccessful.
Drawbacks of Proxies/Proxy Servers
There is a good reason why proxy servers are no longer as popular as they once were. They come with several drawbacks that you should know about if you are thinking of using them:
- The proxy server admin can keep track of user activity quite easily. They can see all the requests that pass through the server, and therefore see what sites a user has been visiting. This is not ideal for anyone looking for a secure and anonymous internet security solution.
- Most proxy servers do not encrypt data. Those considered most secure use SSL certificate encryption, which is hardly ideal – hackers and intelligence agencies can strip away this basic encryption quite easily.
- Proxy server administrators can block access to sites that users may want to access. If, for example, they don't want users accessing social media sites, they can list these among what they consider malicious sites effectively locking out anyone who might need access. This kind of censorship is exactly what VPNs are built to circumvent.
- Proxies have limited servers compared to VPNs which have hundreds or thousands of clients that users can choose from.
VPN vs. Proxy: Which One Should You Choose?
While both setups have benefits and drawbacks, it is more secure to use a VPN than to connect to the internet through a proxy server. VPNs can do the following things that proxy servers cannot:
- A VPN encrypts data using the strongest encryption algorithms. Some proxies encrypt data, but using weak algorithms that can be broken into.
- VPNs offer thousands of servers to choose from, providing a more efficient and reliable way to overcome geoblocks.
- Proxies keep a log of web activity – every information request gets logged in the server along with the IP address that makes the request. If someone wanted to keep track of your web activity all they need to do is get their hands on this log. The best VPNs are very careful about collecting user data. They have a no-logs policy. They indeed collect basic information, but they destroy this after a short time.
- Proxies are often associated with poor performance, especially when many users connect at the same time. Multiple connections slow performance and you'll see messages like “bad gateway” and “failed stream” or “buffering”.
Looking at the pros and cons of proxy servers and VPNs, it's quite clear that when it comes to the question of VPN vs. proxy, a VPN is a much better option.
Conclusion
Both VPNs and proxy servers are security solutions that you can use to stay anonymous online and avoid geoblocks.
However, you'll do much better with a VPN. You have access to any site you want to visit and access to hundreds (usually thousands) of servers to connect through.
While it's true that most VPNs will collect some client data, it's very little, and they are keen to destroy it every few weeks. You don't have this guarantee with proxy servers.
If you are looking for a solid internet security solution, you'll do much better with a VPN.
Recommended VPN's
|
VPN |
Number of Servers |
Number of Devices |
Kill Switch |
Streaming Netflix |
User Logs |
Jurisdiction |
Price (Month) |
| 1,300+ | 10 | ✓ | ✓ | ✖ | United States | $10.00 | |
| 3,200+ | Unlimited | ✓ | ✓ | ✖ | British Virgin Isl. | $12.95 | |
| 6,000+ | 7 | ✓ | ✓ | ✖ | Romania | $12.99 | |
| 5,400+ | 6 | ✓ | ✓ | ✖ | Panama | $11.95 | |
| 3,000+ | 5 | ✓ | ✓ | ✖ | British Virgin Isl. | $12.95 | |
| 700+ | 5 | ✓ | ✓ | ✖ | Switzerland | $12.95 |


